(Schluesselzusatzgeraet – cipher attachment device)
The SZ40/42 was a version of the Geheimschreiber (‘secret writer’) type of cipher machine used on teleprinter (‘teletype’, ‘Fernschreiber’) networks. The SZ40/42 was built by the Lorenz company and it is now common to call the cipher technique used by the machine the ‘Lorenz cipher’.
A photo of the SZ40/42 can be found on the ‘Colossus photos’ page of this website. Some block diagrams can be found on the ‘Colossus downloads’ page.
The SZ40/42 used the ‘Vernam cipher’ rules for combining the five-bit ‘Baudot code’ used by teleprinter transmission techniques. See ‘Colossus - Lorenz cipher i’ page of this website.
The SZ40/42 had twelve wheels with raised or lowered pins. Ten of these wheels were used in two sets of five wheels. These two sets of five wheels generated two streams of key characters which would be combined with the plain language character stream to create the cipher text. The other two wheels gave a pseudo-random pattern to one of the streams of key characters. This pseudo-random pattern was supposed to hide any statistical evidence of the key character streams.
Deciphering reversed the process by using the same settings to generate the same two streams of key characters. Combining these key character streams with the enciphered text stream would wipe out the cipher due to the way the Vernam cipher rules work revealing the plain language message.
Table 1 shows how the plain language message (blue), with distinct character frequencies, is transformed by the cipher machine and its two key character streams, into a stream of enciphered characters (red) all within a narrow frequency band and thus not susceptible to frequency analysis.
Table 1 – Hiding the Plain
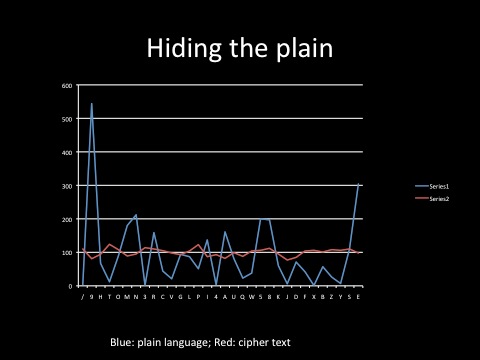
The Bletchley Park codebreakers, led by John Tiltman and aided by Bill Tutte, worked out how the cipher worked and developed ‘hand methods’ of breaking some messages (such as those sent twice with the same ‘wheel settings’).
When more stringent German operating methods blocked this avenue of approach Alan Turing was called in and he recommended a technique known as ‘difference’ or ‘delta’. This looked at the relationship between adjacent characters in the plain or cipher streams and was used for hand breaking of the ’pin settings’ when no other method was available (the pin settings remaining valid for anything between one month and one day). But this method too was blocked by new German procedures.
Bill Tutte developed a theoretical method of breaking the ‘wheel settings’ of each individual message using the delta and stripping the cipher stream down into a series of component streams.
Table 2 - The Statistical Method
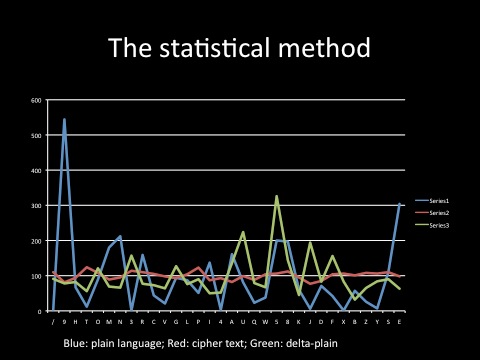
Table 2 shows a third character stream (green) which is derived from the cipher stream (red); this derived stream was known at Bletchley Park as the ‘delta-plain’ and could be identified within the enciphered message using advanced statistical analysis.
However the processing involved in the analysis used was too demanding for human ‘hand methods’, so Max Newman realised that machine methods would be necessary. The first devices used electro-mechanical techniques and proved that mechanisation could solve the cipher – but also proved to be too slow to work in an effective timescale.
A powerful electronic machine, Colossus, was devised by Tom Flowers to analyse these character streams. Ten Colossus machines were built and all were used to crack the messages sent back and forth between Hitler and his army high command – giving the Allies vital strategic intelligence about the Eastern front, the Mediterranean and D-Day.
Many other individuals, including Donald Michie and Jack Good, who extended the work done by Colossus and developed its statistical foundations, also contributed to the overall project. Cracking the Lorenz SZ 40/42 was truly a team achievement.
The graphs in the two tables above have been constructed using the figures reproduced in Appendix E of Colossus: Bletchley Park’s Greatest Secret; all figures based on a single message of 3,200 characters length, transmitted on the Grilse link on 10/1/45
The original source is General Report on Tunny, written just after the end of WWII and now held at the National Archives in Kew, West London (HW5/24 & HW5/25); a facsimile copy is available on http://www.alanturing.net/turing_archive/archive/index/tunnyreportindex.html
(however it should be noted, despite the name of the website hosting the document, it was not written by Turing, but by others including Donald Michie and Jack Good)
Read more about how all this was achieved in
Colossus: Bletchley Park’s Greatest Secret
by Paul Gannon